IPSEC-IKEv1 Packet Flow
Main Mode:-
1 and 2 source and destination port=500
SA payload--->proposals of phase 1
nat-t=set


SA payload--->
protocol id=IPSEC_ESP (type of ipsec vpn)
SPI=0x2BCBFS (used to identify SA)--SPI (internal index number)
phase 2 proposals
nonce payload--->nonce data
hash payload--->hash data
identification payload--->identification data (source pubic ip) clear text
identification payload--->identification data (source proxy id) clear text
3--->The last packet is sent to the remote device to verify the other device is still there and is an active peer.
1 and 2 source and destination port=500
SA payload--->proposals of phase 1
nat-t=set


3 and 4: source and destination port=500 --> the purpose of this packet is to exchange DH secret key
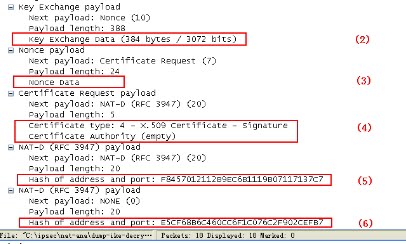
Key Exchange Payload which contains-->key exchange data i.e;(DH secret key)
nonce payload which contains--->nonce data (random Number)
Key Exchange Payload which contains-->key exchange data i.e;(DH secret key)
nonce payload which contains--->nonce data (random Number)
Are Exchanged
NAT-D payload--->Local identification(hash of local original ip and port)
NAT-D payload--->remote identification(hash of remote ip and port)
NAT-D payload--->Local identification(hash of local original ip and port)
NAT-D payload--->remote identification(hash of remote ip and port)
5 and 6: source and destination port=500
identification payload--->identification data (source pubic ip)
hash payload--->hash data (Pre-shared key)
identification payload--->identification data (source pubic ip)
hash payload--->hash data (Pre-shared key)
Source and destination port=4500
(Certificate is also exchanged in these packets only)
Quick Mode:-
exchange type=quick mode
message id=0x0b123456----- >it is same for all packets 1 and 2 in quick mode
this message id is used for identification of previously established phase 1.
all above will be same in all quick mode packets
1 and 2-->hashes/keys negotiated from phase 1 and some phase 2 parameters
message id=0x0b123456----- >it is same for all packets 1 and 2 in quick mode
this message id is used for identification of previously established phase 1.
all above will be same in all quick mode packets
1 and 2-->hashes/keys negotiated from phase 1 and some phase 2 parameters
=====
SA payload--->
protocol id=IPSEC_ESP (type of ipsec vpn)
SPI=0x2BCBFS (used to identify SA)--SPI (internal index number)
phase 2 proposals
nonce payload--->nonce data
hash payload--->hash data
identification payload--->identification data (source pubic ip) clear text
identification payload--->identification data (source proxy id) clear text
3--->The last packet is sent to the remote device to verify the other device is still there and is an active peer.
it contains hash payload--->hash data
Firewall(Private ip)-------------router(Public ip)---------ISP-------Peer device
1)router will do a twice nat or bidirectional nat
2)S2S is formed b/w firewall to peer device not from router to peer device.
3)at firewall src and dest port=4500, sourc ip=private, dest ip=public
at router source port=random port, dest port=4500, sourc ip=public, dest ip=public
4)since source ip and port is changed how peer device knows if It is forming tunnel with right Peer.
It is because of NAT-T where private ip is exchanged in 3 and 4 packet
NAT-D payload--->Local identification(hash of local original ip and hash of remote ip and port)










0 Response to "IPSEC-IKEv1 Packet Flow"
Post a Comment